Developers, testers, and auditors use an application security checklist template to develop more secure applications. They use it to make sure that the software they develop adheres to the highest levels of security standards. This tool specifies all the necessary elements that an application should possess.
Table of Contents
Why should you implement an application security checklist?
Implementing an application security checklist provides several benefits for businesses;
- With the help of an application security checklist, they can determine potential weaknesses and flaws in application code. This as a result reduces the risk of breaches and cyber-attacks.
- The checklist motivates employees to prioritize security in their daily tasks. Thus, it promotes a security culture within the organization.
- It ensures no essential steps are missed during development by allowing consistent and repeatable security measures.
- Along with protecting sensitive data, businesses can build trust and confidence with their customers.
The different types of application security:
Here are the different types of application security;
Authentication
Software developers build authentication procedures into an application to make sure that only authorized users can have access to it. When logging in to an application, the users have to provide a username and password.
Furthermore, more than one form of authentication is required in multi-factor authentication. These may include;
- Something you know (a password)
- Something you have (a mobile device)
- Something you are (a thumbprint or facial recognition)
Authorization
To access and use the application, the user may be authorized after authentication. After that, the system compares the user’s identity with a list of authorized users to validate that a user has permission to access the application. The authentication must be done before authorization.
Encryption
The security measures can protect sensitive data from being used by a cybercriminal when the user is using the application. In cloud-based applications, the traffic that contains sensitive data can be encrypted to keep the data safe.
Logging
Logging can assist in determining who got access to the data and how if there is a security breach in an application.
Application security testing
Application security is tested to make sure that all of these security controls work properly.
Why is it important to build application security standards and policies?
Applications are at the core of both small and large businesses in today’s technology-driven world. On the other hand, increasing technological advances also pose a significant risk to an organization’s security. To safeguard your business from cyber-attacks and unauthorized access, you must build strong application security standards and policies.
Effective application security standards and policies include the following to ensure the highest level of protection for your organization’s data;
- Assessing and identifying potential vulnerabilities
- Mitigating risks
- Ensuring compliance with security regulations
- Incorporating multiple layers of security controls
- Regular vulnerability scanning
- Continuous security testing
Creating an application security checklist template:
In today’s digital world, application security has become a critical issue as cyber threats are posing a significant risk to businesses and organizations. Consider the following steps to create an application security checklist;
Determine the key elements of the checklist
Determine the key components that should be included in the application security checklist before creating the checklist. Some key elements that are crucial for the security of an application are mentioned below;
- Authentication
- Access control
- Input validation
- Encryption
- Error handling
- Data backup
Identify the assessment methodology
An assessment methodology must be included in an application security checklist. It helps to determine and evaluate the vulnerabilities in an application. There are different assessment methodologies that you can use like manual assessment, automated assessment, or a combination of both. It would be recommended to select the most suitable one for your business as each methodology has advantages and disadvantages.
Build a scoring system
In an application security checklist template, a scoring system is important because it assists in prioritizing vulnerabilities. In addition, businesses can prioritize the vulnerabilities that require sudden attention by assigning a score to each vulnerability. Keep in mind that the scoring system should depend on the following;
- The level of risk posed by the vulnerability
- The ease of exploitation
- The potential impact of the vulnerability
Develop a remediation plan
Another critical component of an application security checklist template is a remediation plan. With the help of this component, you can make a roadmap for mitigating vulnerabilities in an application. The remediation plan should include the following details;
- The steps to be followed to fix vulnerabilities
- The timeline for implementing the fixes
- The responsible parties
Update the application security checklist regularly
It is important to update the application security checklist regularly because the threat landscape is changing constantly. Update the checklist to add new threats, vulnerabilities, and assessment methodologies. This way, you make sure that your business includes the latest threats and vulnerabilities.
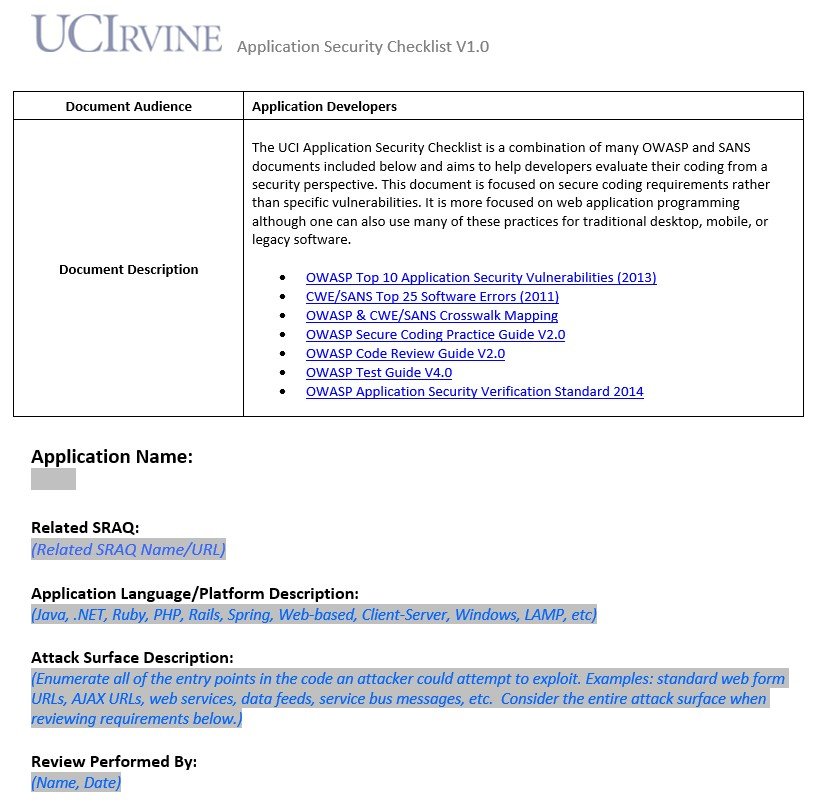
application security checklist template
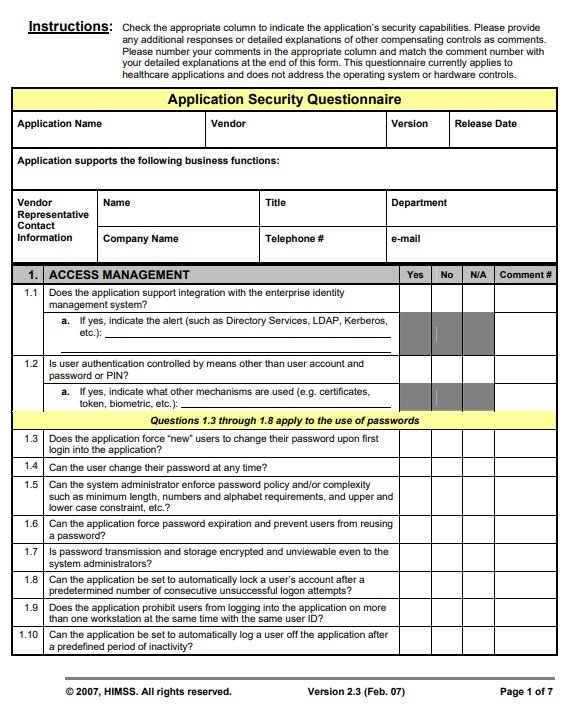
application security questionnaire
certified secure web application security test checklist template
desktop security checklist template free
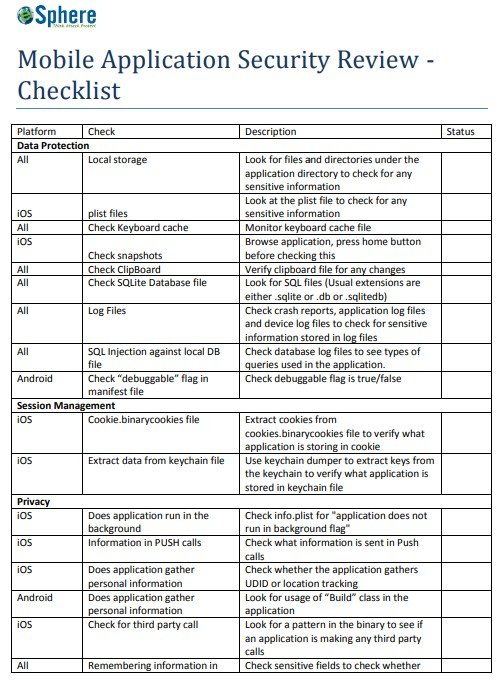
mobile application security checklist template
nada consultants security checklist template
php application security checklist template
secure coding checklist template
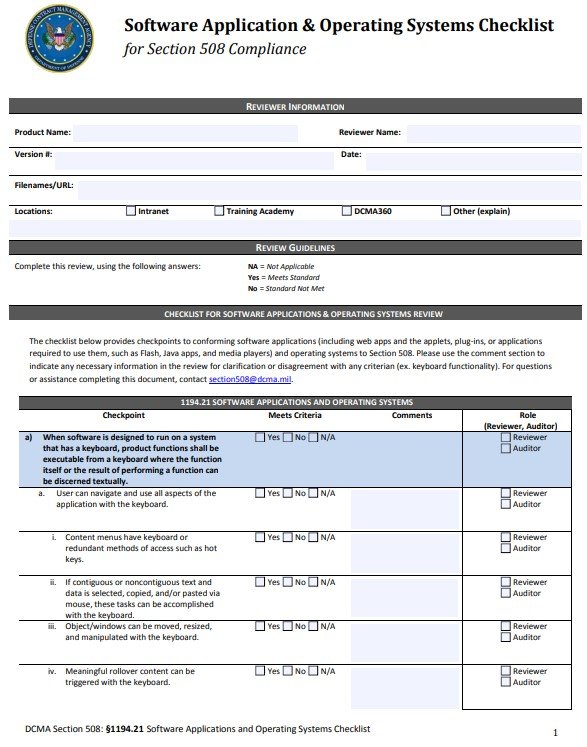
software application operating systems checklist pdf
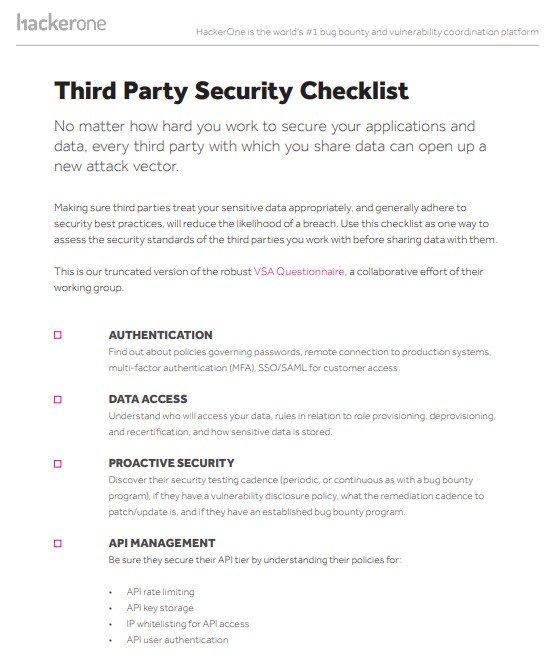
third party security checklist template
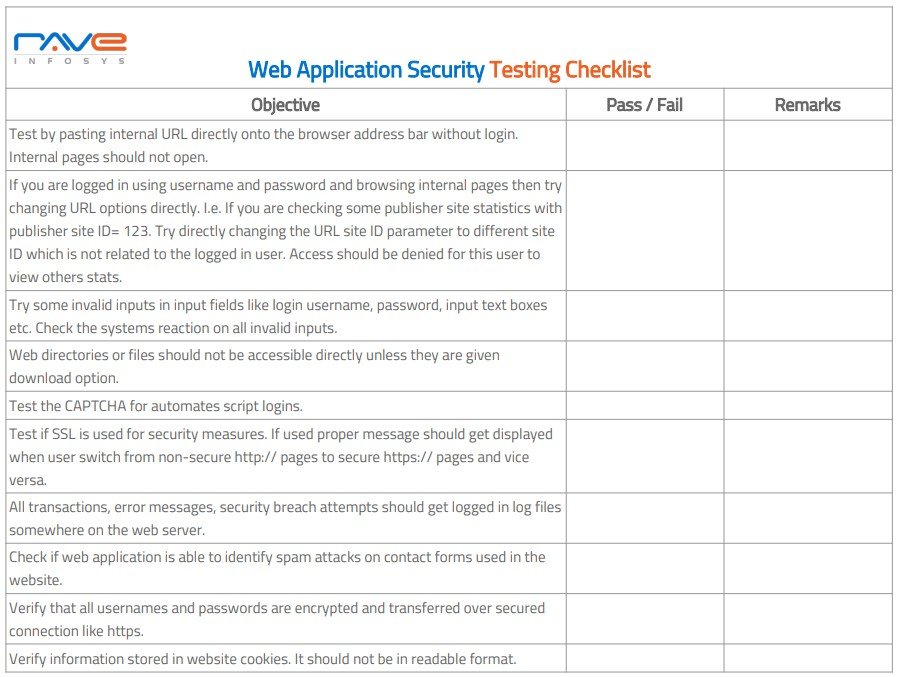
web application security testing checklist template
FAQ’s:
How to ensure the security of an application?
Consider the following tips to keep your application secure;
- Testing
- Use authorization and authentication efficiently
- Utilize the mobile device features
- Minimize attack surface area
- Encrypt sensitive data
- Build a strong API strategy
- Include app security specialists in the project
What are the requirements of application security?
It usually requires hardware, software, and procedures that determine security vulnerabilities.
What are the examples of application security?
A few examples of application security are Firewalls, antivirus systems, and data encryption. They prevent unauthorized users from entering a system.






![Printable Tooth Fairy Certificate Template [PDF]](https://exceltmp.com/wp-content/uploads/2020/09/first-tooth-fairy-certificate-template-150x150.jpg)


![Free Patient Satisfaction Survey Template [Word]](https://exceltmp.com/wp-content/uploads/2021/04/patient-satisfaction-survey-template-150x150.jpg)

